SailPoint Identity Management: Optimize Security&Compliance

In the present era, protecting your company’s information and solutions is crucial. Your organization will be severely harmed if an unidentified user has the availability of business information. These engineers have created SailPoint Cloud, a solution that blends Machine learning and artificial intelligence to combat this. With this Sailpoint, Microsoft Azure Cloud-based services and systems are adequately insulated. Through Sailpoint Training, we can learn about what Sailpoint is, Sailpoint IdentityIQ components, and account aggregation in Sailpoint Identity Management.
What is Sailpoint?
Sailpoint is indeed an automating kind of identity management that lowers the expense and complexity of identity management for users while also giving them access. Sailpoint is a portable, lightweight application. It is said to be an identity management solution as it has more functionality than identity management. IdentityIQ is provided by Sailpoint and is known as the IdentityIQ war-file. Most of the application components are contained in this war file.
Sailpoint IdentityIQ components
Compliance Manager.
SailPoint Compliance Manager automates standard auditing, surveillance, and maintenance operations by combining identity methods like Access certification as well as Policy enforcement. Compliance Manager assists in the prioritizing of the most critical regulatory duties and concentrates limits on the persons, technology, and access privileges that are the most dangerous.
Lifecycle Manager.
SailPoint IdentityIQ Lifecycle Manager allows enterprise users to request access and restore passwords from a centralized, user-friendly platform. IdentityIQ Lifecycle Manager ensures all customers have just the most essential requirements of accessibility for the job function by providing certain strategies.
Governance Platform.
SailPoint’s IdentityIQ Governance Framework centralizes identity data, aggregates company procedures, models roles, and constructively manages customer and resources risk factors. Access queries, lifecycle management, and licensing are just a few of the critical identity business activities that can benefit from these advanced techniques.
User Provisioning.
The SailPoint IdentityIQ Provisioning Broker serves as a link between compliance and customer lifecycle procedures, providing for continuous user interface design and methods at the corporate level that are separate from a change in technology.
In SailPoint IIQ, what is Aggregation?
IdentityIQ’s approach for creating and upgrading Identity Cubes that include account, characteristic, and authorization data that can be retrieved via bespoke Applications. Account aggregation is analogous to balancing in an identity management solution. Tasks are in charge of account aggregation. This is accomplished by creating and implementing reusable Account Aggregation routines.
The method of pulling information from the targeted app is known as SailPoint Aggregation. There are two categories of data that can be used:
- Account data refers to information about users who have accounts in a specific application.
- The group data identifies the various capabilities that IDs have in the target application.
The aggregation of SailPoints is set up during the application’s onboarding process. The frequency with which the targeted application is fetched or polled is measured as a function of the company requirements. In Sailpoint IIQ Tasks, such aggregation can be set up.
Compilation of Aggregation Accounts
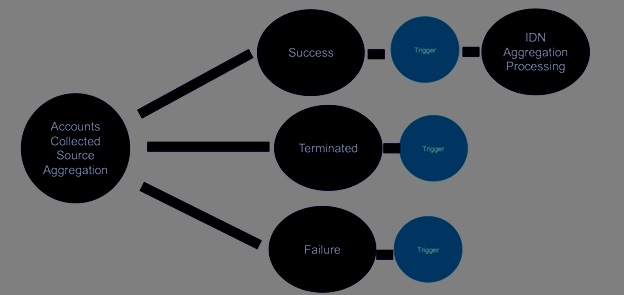
To enable efficient monitoring features, the technology has added an event prompt to the Source Aggregation workflow. For enhanced identity governance, this ensures that account aggregations are functioning as planned and also that identity data constantly represents current source account data.
Following the complete collection of the initial accounts in the data source during aggregation, this activity trigger could indeed:
- Notify a network administrator whether IdentityNow was capable of connecting towards the source file and gathering source accounts effectively.
- Whenever the aggregation is deliberately discontinued during the account acquisition process, notify an administrator.
- Alert an administrator or systems (for example, PagerDuty) if IdentityNow failed to harvest accounts throughout aggregation and also that the source system requires remediation.
Prerequisites for Getting Started
- An oAuth client with the ORG ADMIN authority set.
- An org that has a Source having a Direct Connection set up.
The number of accounts that have been introduced, updated, or withdrawn can be discovered using Aggregations, which link to a source and aggregate account information from it. The aggregate of entitlements is not included in this event trigger.
The activity of the source account is summarised in statistics, such as:
“stats”: {
“scanned”: 200,
“unchanged”: 190,
“changed”: 6,
“added”: 4,
“removed”: 3
}
There will be ten altered profiles in this case (scanned (200) – unchanged – (190)). Accounts that have been altered comprise accounts that have been added (6) and profiles that have been changed (4), totaling 10 accounts. Based on the source, deleted profiles may not even be incorporated into the total of changed accounts. In this case, removed (3) might well be regarded as a changed account by some sources, resulting in a scanned count of 203 rather than 200.
Even if no accounts are changed, the action trigger would occur. The scanned entities in the answer will be matched by the unchanged count. When there are problems linking to the sources while aggregation, this event trigger comes in handy.
The timestamps for the start and finish are all in ISO8601 style.
Aggregation Status
The success of the Aggregation After successful account gathering, aggregation can proceed to the next phase.
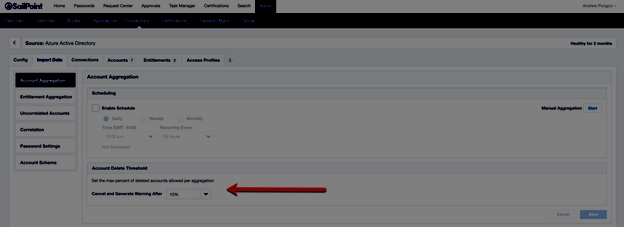
Even during the account acquisition process, Termination aggregation was turned off. When such an account closure threshold is reached, aggregation could be turned off. For example, the source has a default account deletion threshold of 10%, and if the amount of removed accounts in the previous example is 21 (greater than 10% of scanned accounts (200), the aggregate is canceled.
Schema for Input
The input schema specifies the content of your subscription. The trigger has given an example of input:
{
“stats”: {
“scanned”: 200,
“unchanged”: 190,
“changed”: 6,
“added”: 4,
“removed”: 3
},
“warnings”: [
“Account skipped”
],
“started”: “2020-06-29T22:01:50.474Z”,
“source”: {
“id”: “4e4d982dddff4267ab12f0f1e72b5a6d”,
“name”: “Corporate Active Directory”,
“type”: “SOURCE”
},
“completed”: “2020-06-29T22:02:04.090Z”,
“errors”: [],
“status”: “Success”
}
- status – The aggregation’s current state. “Success,” “Failed,” or “Terminated” are the most common options.
- warnings – During the aggregation, a set of warning messages was collected.
- completed – When the aggregation was finished (either successfully or not).
- unchanged – The number of accounts that were previously active but did not change.
- source – A pointer to the source that is performing the aggregation. Are used to receive more data (like connector, operator, VA cluster, etc)
- started – The start time of the aggregate.
- removed – The number of accounts that were formerly active but are no longer active (thus getting eliminated).
- errors – A record of error codes gathered during the aggregation.
- stats – These are the total statistics gathered during the aggregation process. The number of accounts that have been scanned or iterated over.
- change – The number of users that were formerly active but have since changed.
- added – The number of users that have been added.
Conclusion
The aggregation of SailPoints has been explained in detail in this article. Maintaining information access in today’s sophisticated, data-driven environment is a task that requires far more from the Identity and Access Management (IAM) systems than ever before. Through the use of this technology, businesses may successfully prevent unauthorized access permissions and limit the danger of critical data loss.